What is CSPM and How Does It Differ From DSPM?
That’s all we need, some might think: another security acronym (or two). However, CSPM (Cloud Security Posture Management) and DSPM (Data Security Posture Management) are far from being two new names on the block – they are the foundational ways critical information gets secured in the cloud.
While distinct, they both protect serverless data and both serve the same end of eliminating cloud security breaches. However, their approaches are different, and therein may lie the key to their success when combined.
For the uninitiated, here is a crash course in the basics of Cloud Security Posture Management, how it differs from Data Security Posture Management, and what can be accomplished by combining the two.
What is Cloud Security Posture Management (CSPM)?
CSPM is an approach to making cloud infrastructures safer, whether these be public cloud, hybrid cloud, or multi-cloud environments. As Gartner defines, CSPM “consists of offerings that continuously manage IaaS and PaaS security posture through prevention, detection, and response to cloud infrastructure risks.”
Some things a CSPM tool might monitor for include:
- Misconfigurations
- Illicit data access
- Malware instances
- Insider cloud threats
- Compliance infractions
CSPM looks for gaps in cloud protection and seeks to fill them, differing from point solutions like EDR (Endpoint Detection and Response), API security tools, or DLP (Data Loss Prevention) in that it looks to protect the entire cloud environment, not just a part. This comprehensive approach means that:
- Teams get complete visibility across their entire cloud infrastructure.
- Discovered threats are prioritized based on how much of a risk they present compared to other threats so teams can get to what matters most first.
- Risks can be discovered earlier in the attack cycle, averting disaster.
- Organizations have extra help in meeting comprehensive data protection requirements like GDPR and CCPA and aligning with best-practice frameworks like NIST and the CIS Controls.
When do you want to use CSPM? When you want to bolster cloud infrastructure and prevent cloud misconfiguration errors that could lead to data breaches. Remember, this locks your jewelry store’s outer and inner doors and ensures the structure is sound against outside attackers. Research indicates that a CSPM can reduce cloud-based security incidents attributable to misconfigurations by 80%.
How Is CSPM Different from Data Security Posture Management (DSPM)?
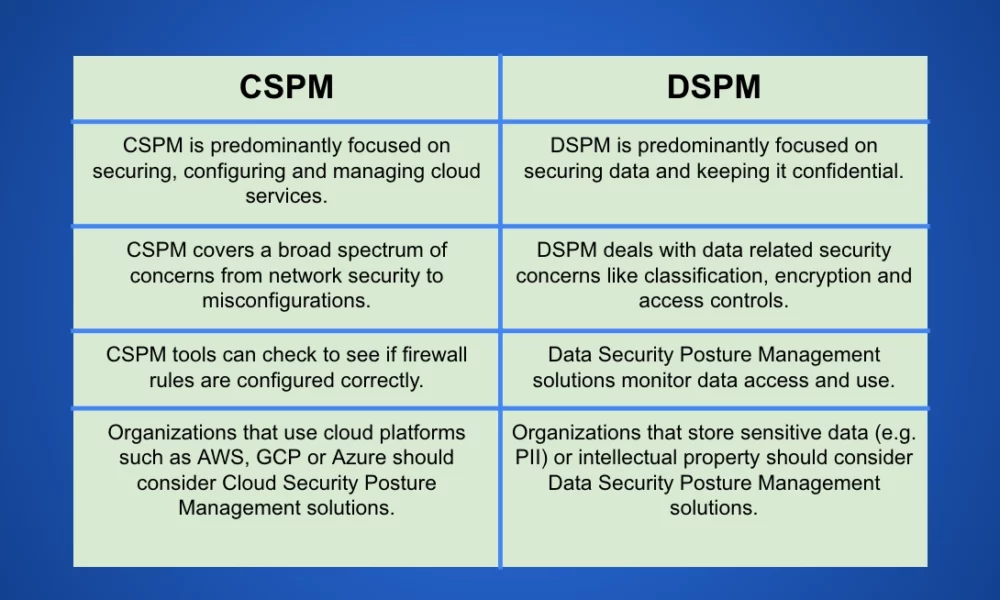
CSPM differs from Data Security Posture Management (DSPM) in its scope. While CSPM protects the infrastructure of the cloud (to secure the data inside), DSPM provides an additional layer of defense for the data itself.
When not stored on-premises, sensitive data still needs to be kept track of and secured (perhaps in those cases more than any). Data Security Posture Management does precisely that, transcending mere data cataloging to include the finding, classification, and security of data as well. Just like the doors of a jewelry store need to be locked at night (we’ll call that CSPM), the actual jewels must also be secured in locked boxes, inventoried, and monitored to ensure they are consistently safe. That’s DSPM.
As noted by IBM, Data Security Posture Management is “sometimes referred to as ‘data first’ security because it inverts the protection model embraced by other cybersecurity technologies and practices.”
With this single-minded focus on data, teams that utilize DSPM can:
- Gain visibility into where (in the cloud) their sensitive data is stored.
- Flag risks that could lead to data exfiltration, like misconfigurations and vulnerabilities.
- Monitor data in real-time to quickly respond to threats.
- Better comply with data security standards like GDPR, PCI DSS, and HIPAA.
- Leverage machine learning and automation to spot hard-to-catch malicious behaviors, monitor data flows, perform risk assessments more quickly, and even gain insights into mitigative steps to perform next to best prevent data loss.
When do you want to use DSPM? DSPM is ideal if the top priority is safeguarding sensitive data. Safeguarding means not only following good practices, but also ensuring good data governance, and that you are meeting regulatory requirements like GDPR or HIPAA. Going back to our analogy, this is like putting the jewels themselves in locked boxes, ensuring all valuables in the store are located and protected according to value, training security cameras on them nonstop, and prioritizing which jewels need increased security the most.
Side-by-Side: CSPM vs. DSPM
For a side-by-side comparison, here are a few points that really showcase the differences between Cloud Security Posture Management and Data Security Posture Management – both of which are necessary for the strongest defense-in-depth cloud security approach.
- A security overview of your entire cloud environment.
- Monitors cloud configurations to make sure they’re all above-board compliance-wise, making sure your cloud architecture passes muster on its next audit.
- The ability to scale cloud security when you scale cloud resources.
- Preventing cloud-based attacks before they occur, due to finding things like misconfigurations, security threats, and compliance issues early in the game.
DSPM:
- The ability to find sensitive data hiding across various cloud architectures.
- Round-the-cloud data monitoring that never turns off, so there’s no lag time between catching a culprit and mounting a defense.
- Granular data policies that make complying with regulatory frameworks like GDPR, NIST, HIPAA, and more a much simpler process.
- Automation and machine learning that enables teams to drastically speed up the process of assessing risks.
While CSPM is about overall cloud defense and general prevention, DSPM is about following data points around with specific policies and protections and jumping into action when something happens to threaten those cloud-based data assets.
Which is more important? In a zero-trust cloud security strategy, it can be argued that the answer is “neither.” Both are needed for different aspects of the cloud data security lifecycle. The only question is, where to start?
About the author:
An ardent believer in personal data privacy and the technology behind it, Katrina Thompson is a freelance writer leaning into encryption, data privacy legislation, and the intersection of information technology and human rights. She has written for Bora, Venafi, Tripwire, and many other sites.





